ANDROIDOS_FAKEBANK.A
June 18, 2013
THREAT SUBTYPE:
Information Stealer
PLATFORM:
Android OS
OVERALL RISK RATING:
DAMAGE POTENTIAL:
DISTRIBUTION POTENTIAL:
REPORTED INFECTION:


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
TECHNICAL DETAILS
NOTES:
When the user installs this malware, it creates an icon like Google Play.
It contains the following malware APKs in its assets folder:
- 1.apk
- 2.apk
- 3.apk
- 4.apk
- 5.apk
- 6.apk
- 7.apk
- 8.apk
Once started, the FakeBank malware copies the said APKs to the SD card.
It then installs the abovementioned APKs. If the phone is rooted, FakeBank silently uninstalls the following by using the same icon and UI:
- com.kbcard.kbkookmincard
- com.ibk.spbs
- com.smg.spbs
com.kbcard.kbkookmincard, com.ibk.spbs, and com.smg.spbs are certain banking applictaions.
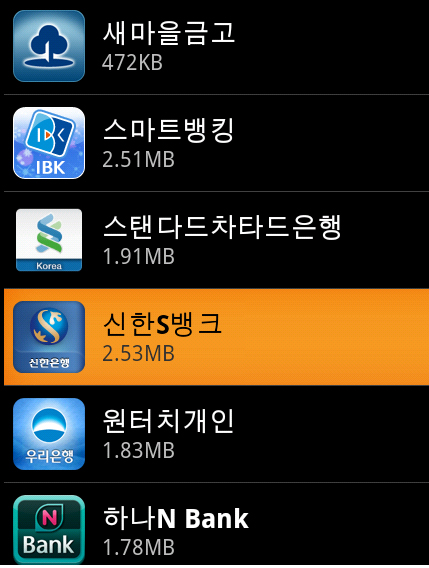
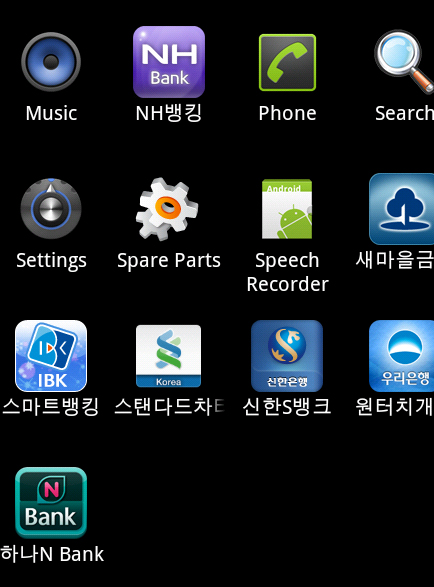
When users start the disguised smart banking apps and fill in their account information, the fake Smart Banking apps send private account information , received SMS, and call log to the remote server,http://{BLOCKED}s.com/Add[xxx].aspx.