WORM_PROLACO.EK
NORTON: Trojan.Bredolab; KASPERSKY: Trojan.Win32.Buzus.gdef; SUNBELT: Trojan.Win32.Meredrop
Windows 2000, XP, Server 2003


Threat Type: Worm
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
This worm arrives as attachment to mass-mailed email messages. It arrives via removable drives.
It adds registry entries to enable its automatic execution at every system startup.
It drops an AUTORUN.INF file to automatically execute the copies it drops when a user accesses the drives of an affected system.
It also has rootkit capabilities, which enables it to hide its processes and files from the user.
It modifies the affected system's HOSTS files. This prevents users from accessing certain websites.
TECHNICAL DETAILS
Arrival Details
This worm arrives as attachment to mass-mailed email messages.
It arrives via removable drives.
It may arrive via network shares.
Installation
This worm drops and executes the following files:
- %System%\sta-css.exe - TROJ_HILOTI.SMEO
- %System%\sta-cpe.exe - TROJ_FAKEAV.EKA
(Note: %System% is the Windows system folder, which is usually C:\Windows\System on Windows 98 and ME, C:\WINNT\System32 on Windows NT and 2000, or C:\Windows\System32 on Windows XP and Server 2003.)
It drops the following copies of itself into the affected system:
- %System%\PCSuite.exe
(Note: %System% is the Windows system folder, which is usually C:\Windows\System on Windows 98 and ME, C:\WINNT\System32 on Windows NT and 2000, or C:\Windows\System32 on Windows XP and Server 2003.)
It adds the following mutexes to ensure that only one of its copies runs at any one time:
- PCSuite.exe{random characters}
Autostart Technique
This worm adds the following registry entries to enable its automatic execution at every system startup:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Run
Nokia Launch Application = %System%\PCSuite.exe
Other System Modifications
This worm adds the following registry keys:
HKEY_CURRENT_USER\Software\Nokia4
HKEY_LOCAL_MACHINE\Software\Nokia4
It adds the following registry entries as part of its installation routine:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Explorer
nok01 = {month of execution}
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Explorer
nok02 = {day of execution}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Security Center
UACDisableNotify = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\policies\
system
EnableLUA = 0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\SharedAccess\Parameters\
FirewallPolicy\StandardProfile\AuthorizedApplications\
List
%System%\PCSuite.exe = %System%\PCSuite.exe:*:Enabled:Explorer
Propagation
This worm creates the following folders in all removable drives:
- [dirve letter]:\RECYCLER
- [dirve letter]:\RECYCLER\S-1-6-21-2434476521-1645641927-702000330-1542
It drops copies of itself into the following folders used in peer-to-peer (P2P) networks:
- %User Profile%My Documents\Frostwire\shared
- %Program Files%\icq\shared folder\
- %Program Files%\grokster\my grokster\
- %Program Files%\emule\incoming\
- %Program Files%\morpheus\my shared folder\
- %Program Files%\limewire\shared\
- %Program Files%\tesla\files\
- %Program Files%\winmx\shared\
- %System Root%\Downloads\
- Kazaa Download Directory
- DC++ Download Directory
(Note: %User Profile% is the current user's profile folder, which is usually C:\Windows\Profiles\{user name} on Windows 98 and ME, C:\WINNT\Profiles\{user name} on Windows NT, and C:\Documents and Settings\{user name} on Windows 2000, XP, and Server 2003.. %Program Files% is the default Program Files folder, usually C:\Program Files.. %System Root% is the root folder, which is usually C:\. It is also where the operating system is located.)
It drops the following copy(ies) of itself in all removable drives:
- [dirve letter]:\RECYCLER\S-1-6-21-2434476521-1645641927-702000330-1542\redmond.exe
It drops an AUTORUN.INF file to automatically execute the copies it drops when a user accesses the drives of an affected system.
The said .INF file contains the following strings:
[autorun]
open=RECYCLER\S-1-6-21-2434476521-1645641927-702000330-1542\redmond.exe
icon=%SystemRoot%\system32\SHELL32.dll,4
action=Open folder to view files
shell\open=Open
shell\open\command=RECYCLER\S-1-6-21-2434476521-1645641927-702000330-1542\redmond.exe
shell\open\default=1
It gathers target email addresses from files with the following extensions:
- ·txt
- ·htm
- ·xml
- ·php
- ·asp
- ·dbx
- ·log
- ·nfo
- ·lst
- ·wpd
- ·wps
- ·xls
- ·doc
- ·wab
- ·rtf
It avoids sending email messages to addresses containing the following strings:
- berkeley
- unix
- bsd
- mit.e
- gnu
- fsf.
- ibm.com
- debian
- kernel
- linux
- fido
- usenet
- iana
- ietf
- rfc-ed
- sendmail
- arin.
- sun.com
- isc.o
- secur
- acketst
- pgp
- apache
- gimp
- tanford.e
- utgers.ed
- mozilla
- firefox
- suse
- redhat
- sourceforge
- slashdot
- samba
- cisco
- syman
- panda
- avira
- f-secure
- sopho
- www.ca.com
- ahnlab
- novirusthanks
- prevx
- drweb
- bitdefender
- clamav
- eset.com
- ikarus
- mcafee
- kaspersky
- virusbuster
- badware
- immunityinc.com
- avg.comsysinternals
- borlan
- inpris
- lavasoft
- jgsoft
- ghisler.com
- wireshark
- winpcap
- acdnet.com
- acdsystems.com
- acd-group
- bpsoft.com
- buyrar.com
- bluewin.ch
- quebecor.com
- alcatel-lucent.com
- ssh.com
- winamp
- nullsoft.org
- example
- mydomai
- nodomai
- ruslis
- virus
- .gov
- gov.
- .mil
- messagelabs
- honeynet
- honeypot
- security
- idefense
- qualys
- root
- info
- samples
- postmaster
- webmaster
- noone
- nobody
- nothing
- anyone
- someone
- your
- you
- me
- bugs
- rating
- site
- contact
- soft
- no
- somebody
- privacy
- service
- help
- not
- submit
- sales
- ca
- gold-certs
- the.bat
- page
- admin
- icrosoft
- support
- ntivi
- unix
- bsd
- linux
- listserv
- websense
- certific
- security
- spam
- sp
- spam
- www
- secur
- abuse
Rootkit Capabilities
This worm also has rootkit capabilities, which enables it to hide its processes and files from the user.
Process Termination
This worm terminates the following services if found on the affected system:
- aswupdsv
- avast! Antivirus
- avast! Mail Scanner
- avast! Web Scanner
- avg8wd
- avg8emc
- antivirservice
- AntiVirSchedulerService
- XCOMM
- LIVESRV
- bdss
- scan
- VSSERV
- Arrakis3
- CaCCProvSP
- CSIScanner
- Emproxy
- McAfee HackerWatch Service
- MCNASVC
- MPFSERVICE
- MPS9
- mcpromg
- mcproxy
- mcshield
- mcredirector
- mcODS
- mcmscsvc
- msk80service
- mcsysmon
- mcmisupdmgr
- Ehttpsrv
- ekrn
- sdauxservice
- sdcodeservice
- ThreatFire
- sbamsvc
- FPAVServer
- RSCCenter
- RSRavMon
- K7EmlPxy
- K7RTScan
- K7TSMngr
- navapsvc
- npfmntor
- nscservice
- liveupdate
- Norton AntiVirus
- LiveUpdate Notice Service
- SAVScan
- Symantec Core
- ccEvtMgr
- sndsrvc
- ccprox
- ccpwdsvc
- ccsetmgr
- spbbcsvc
- MBAMService
- Savservice
- Savadminservice
- Sophos Autoupdate Service
- Sophos Agent
- Sophos Certification Manager
- Sophos Management Service
- Sophos Message Router
- PAVSVR
- PAVFNSVR
- GWMSRV
- PSHOST
- PSIMSVC
- PAVPRSRV
- PSKSVCRETAIL
- PANDA SOFTWARE CONTROLLER
- TPSRV
- WinDefend
- wscsvc
- ERSvc
- WerSvc
- AVP
It terminates the following processes if found running in the affected system's memory:
- mcvsshld.exe
- McProxy.exe
- mps.exe
- mcmscsvc.exe
- mcpromgr.exe
- McNASvc.exe
- mcagent.exe
- Mcshield.exe
- HWAPI.exe
- RedirSvc.exe
- emproxy.exe
- mcsysmon.exe
- mcods.exe
- MpfSrv.exe
- msksrver.exe
- mskagent.exe
- ccsvchst.exe
- PShost.exe
- TPSRV.exe
- avciman.exe
- APvxdwin.exe
- Pavbckpt.exe
- iface.exe
- PSCtrlS.exe
- PavFnSvr.exe
- prevx.exe
- PavPrSrv.exe
- PsIMSVC.exe
- psksvc.exe
- PAVSRV51.exe
- AVENGINE.exe
- Webproxy.exe
- SrvLoad.exe
- avgnt.exe
- guardgui.exe
- avcenter.exe
- avguard.exe
- avgwdsvc.exe
- avgrsx.exe
- avgtray.exe
- avgemc.exe
- avgcsrvx.exe
- avgui.exe
- xcommsvr.exe
- seccenter.exe
- bdss.exe
- bdagent.exe
- livesrv.exe
- ekrn.exe
- egui.exe
- sbamtray.exe
- sbamui.exe
- K7TSMngr.exe
- K7RTScan.exe
- K7EmlPxy.exe
- K7SysTry.exe
- K7TSecurity.exe
- drweb32w.exe
- drwebupw.exe
- spidergui.exe
- avp.exe
- avp.exe
- mbam.exe
- pccnt.exe
- NTRtScan.exe
- TmListen.exe
- FPWin.exe
- FprotTray.exe
- FPAVServer.exe
- SavService.exe
- SavMain.exe
- AlMon.exe
- SavAdminService.exe
- ALSvc.exe
- SbeConsole.exe
- Rav.exe
- RavTask.exe
- RavMon.exe
- RavmonD.exe
- RavStub.exe
- CCenter.exe
- isafe.exe
- vsserv.exe
- vetmsg.exe
- ashdisp.exe
- ashserv.exe
Dropping Routine
This worm sets the attributes of its dropped file(s) to the following:
- Hidden
- Read-Only
- System
HOSTS File Modification
This worm adds the following strings to the Windows HOSTS file:
- eset.com
- f-secure.com
- sophos.com
- virustotal.com
- hispasec.com
- mcafee.com
- mast.mcafee.com
- networkassociates.com
- download.mcafee.com
- dispatch.mcafee.com
- nai.com
- us.mcafee.com
- symantec.com
- securityresponse.symantec.com
- liveupdate.symantecliveupdate.com
- symantec.com
- liveupdate.symantec.com
- customer.symantec.com
- sophos.com
- viruslist.com
- avp.com
- kaspersky.com
- kaspersky-labs.com
- ca.com
- my-etrust.com
- trendmicro.com
- free-av.com
- authentium.com
- avg.com
- ewido.com
- grisoft.com
- global.ahnlab.com
- avast.com
- bitdefender.com
- quickheal.com
- aladdin.com
- ikarus-software.at
- pandasecurity.com
- virus-buster.com
Other Details
This worm connects to the following URL(s) to get the affected system's IP address:
- http://{BLOCKED}myip.com/automation/n09230945.asp
It did not exhibit backdoor routines during testing.
It does the following:
- This worm checks if Mozilla Thunderbird is installed in the affected system. It will check for the SMTP server used by this application by checking the file prefs.js and use it to send email messages containing a copy of itself to harvested email addresses.
- It checks for the presence of the following registry entry to check for SMTP server used in the affected system:
HKEY_CURRENT_USER\Software\Microsoft\Internet Account Manager\Accounts
SMTP Server = "" If no SMTP servers are found from the abovementioned routines, it tries to guess the SMTP Simple Mail Transfer Protocol (SMTP) server of the affected system, using the gathered domain name and the following prefixes: - gate.
- mail.
- mail1.
- mx.
- mx1.
- mxs.
- ns.
- relay.
- smtp.
- It then creates threads that are used to create its own SMTP engine.
- The said engine uses the SMTP servers gathered from the machine and sends email messages containing a copy of itself to email addresses gathered from the abovementioned routine. The said messages have the following appearance:
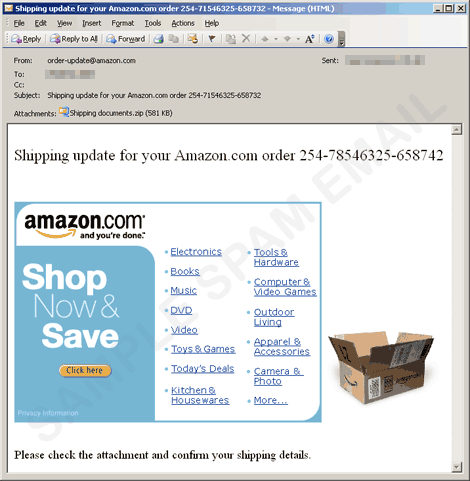
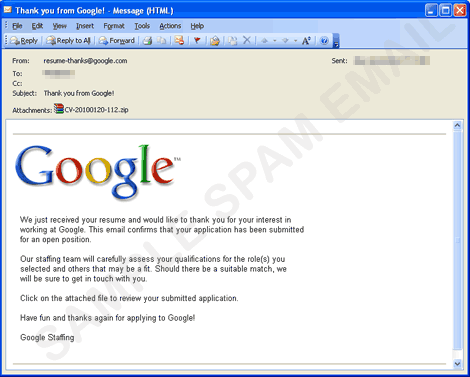
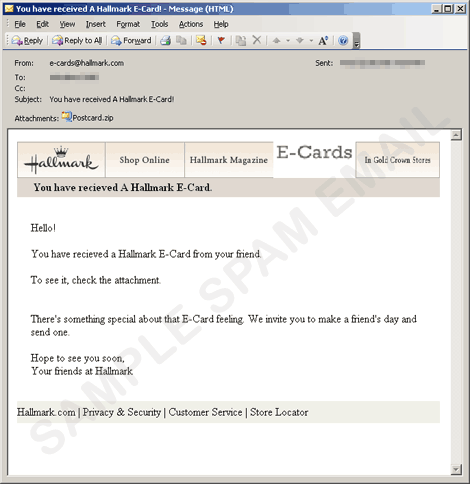
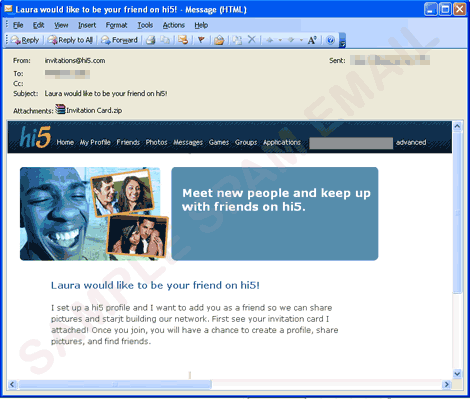
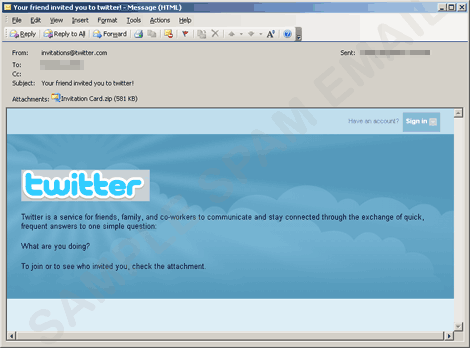
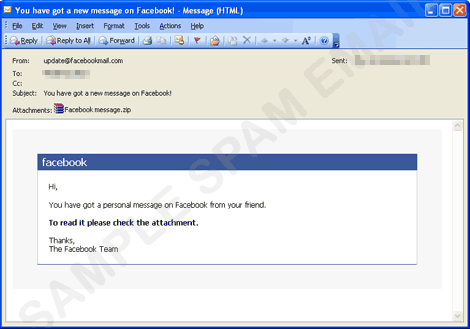
- It can also send an email purportedly from Bacrlays Bank asking for a verification. Clicking the link will direct users to a fake login page.

- It checks for the location of the Windows Address Book by querying the following registry key to gather email addresses:
HKEY_CURRENT_USER\Software\Microsoft\wab\wab4\{WAB file name}
- This malware deletes files associated with the following registry entries:
HKEY_LOCAL_MACHINE\SOFTWARE\McAfee\AVEngine
szInstallDir = "{path}\mcshield.exe"HKEY_LOCAL_MACHINE\SOFTWARE\Malwarebytes' Anti-Malware
InstallPath = {path}\*.*" - It also deletes files in the following folder:
- %Program Files\Prevx
- It deletes the following autorun registry values related to AV software:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
SBAMTray
sbamui
cctray
CAVRID
BDAgent
egui
avast!
AVG8_TRAY
ISTray
K7SystemTray
K7TSStart
SpIDerMail
DrWebScheduler
OfficeScanNT Monitor
SpamBlocker
Spam Blocker for Outlook Express
F-PROT Antivirus Tray application
RavTask
APVXDWIN
SCANINICIO
McENUI
MskAgentexe
Windows Defender - It propagates via Internet servers by querying the following registry entry to get the directory of Internet Information Services and Apache Application:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\InetStp
PathWWWRoot = " "HKEY_LOCAL_MACHINE\SOFTWARE\Apache Software Foundation\Apache\{application}
ServerRoot = " "It will then drop a copy of itself in the directories as ms09-067.exe. It will also drop the file index.htm in the said directories to display the following page upon accessing the servers:
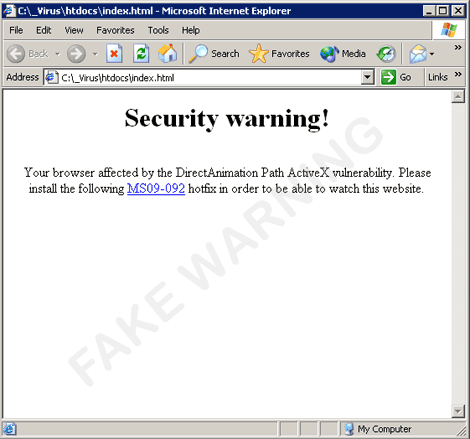
- It uses the following file names for its dropped copies in P2P shares:
- Ad-aware 2010.exe
- Adobe Acrobat Reader keygen.exe
- Adobe Illustrator CS4 crack.exe
- Adobe Photoshop CS5 crack.exe
- Alcohol 120 v1.9.7.exe
- Anti-Porn v13.5.12.29.exe
- AnyDVD HD v.6.3.1.8 Beta incl crack.exe
- Ashampoo Snap 3.02.exe
- AVS Video Converter v6.3.1.365 CRACKED.exe
- BitDefender AntiVirus 2010 Keygen.exe
- Blaze DVD Player Pro v6.52.exe
- CleanMyPC Registry Cleaner v6.02.exe
- Daemon Tools Pro 4.50.exe
- Divx Pro 7 + keymaker.exe
- Download Accelerator Plus v9.exe
- Download Boost 2.0.exe
- DVD Tools Nero 10.5.6.0.exe
- G-Force Platinum v3.7.5.exe
- Google SketchUp 7.1 Pro.exe
- Grand Theft Auto Episodes From Liberty City 2010.exe
- Image Size Reducer Pro v1.0.1.exe
- Internet Download Manager V5.exe
- K-Lite Mega Codec v5.5.1.exe
- K-Lite Mega Codec v5.6.1 Portable.exe
- Kaspersky AntiVirus 2010 crack.exe
- LimeWire Pro v4.18.3.exe
- MagicISO Magic ISO Maker v5.5.0276 Cracked.exe
- McAfee Total Protection 2010.exe
- Microsoft.Windows 7 ULTIMATE FINAL activator+keygen x86.exe
- Motorola, nokia, ericsson mobil phone tools.exe
- Mp3 Splitter and Joiner Pro v3.48.exe
- Myspace theme collection.exe
- Nero 9 9.2.6.0 keygen.exe
- Norton Anti-Virus 2010 crack.exe
- Norton Internet Security 2010 crack.exe
- PDF password remover (works with all acrobat reader).exe
- PDF to Word Converter 3.0.exe
- PDF Unlocker v2.0.3.exe
- PDF-XChange Pro.exe
- Power ISO v4.2 + keygen axxo.exe
- Rapidshare Auto Downloader 3.8.exe
- RapidShare Killer AIO 2010.exe
- Sony Vegas Pro v9.0a incl crack.exe
- Sophos antivirus updater bypass.exe
- Starcraft2 battle.net key generator.exe
- Starcraft2 battle.net keys.txt.exe
- Starcraft2 REGION-UNLOCKER.exe
- Starcraft2 SERVER-CHANGER.exe
- Starcraft2.exe
- Super Utilities Pro 2009 11.0.exe
- Total Commander7 license+keygen.exe
- Trojan Killer v2.9.4173.exe
- Tuneup Ultilities 2010.exe
- Twitter FriendAdder 2.1.1.exe
- Uniblue RegistryBooster 2010.exe
- VmWare 7.0 keygen.exe
- VmWare keygen.exe
- Winamp.Pro.v7.33.PowerPack.Portable+installer.exe
- Windows 7 Ultimate keygen.exe
- Windows 2008 Enterprise Server VMWare Virtual Machine.exe
- Windows XP PRO Corp SP3 valid-key generator.exe
- Windows2008 keygen and activator.exe
- WinRAR v3.x keygen RaZoR.exe
- Youtube Music Downloader 1.0.exe
- YouTubeGet 5.4.exe
SOLUTION
Step 1
For Windows ME and XP users, before doing any scans, please make sure you disable System Restore to allow full scanning of your computer.
Step 2
Remove malware files dropped/downloaded by WORM_PROLACO.EK
- TROJ_FAKEAV.EKA
Step 3
Restart in Safe Mode
Step 4
Delete this registry key
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer"s registry.
- In HKEY_CURRENT_USER\Software
- Nokia4
- Nokia4
- In HKEY_LOCAL_MACHINE\Software
- Nokia4
- Nokia4
Step 5
Delete this registry value
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this Microsoft article first before modifying your computer"s registry.
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Nokia Launch Application = %System%\PCSuite.exe
- Nokia Launch Application = %System%\PCSuite.exe
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer
- nok01 = {month of execution}
- nok02 = {day of execution}
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center
- UACDisableNotify = 1
- UACDisableNotify = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system
- EnableLUA = 0
- EnableLUA = 0
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List
- %System%\PCSuite.exe = %System%\PCSuite.exe:*:Enabled:Explorer
- %System%\PCSuite.exe = %System%\PCSuite.exe:*:Enabled:Explorer
Step 6
Search and delete AUTORUN.INF files created by WORM_PROLACO.EK that contain these strings
shellexecute=wlan.exe
action=Open folder to view files
shell\default=Open
shell\default\command=wlan.exe
shell=default
Step 7
Search and delete this folder
Step 8
Remove these strings added by the malware/grayware/spyware in the HOSTS file
Step 9
Restore this file from backup only Microsoft-related files will be restored. If this malware/grayware/spyware also deleted files related to programs that are not from Microsoft, please reinstall those programs on you computer again.
NOTE: This solution step is also used to restore the deleted registry keys/entries.
- %Program Files%\Prevx
- Malwarebytes' Anti-Malware
- McAfee
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run SBAMTray
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run sbamui
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run cctray
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run CAVRID
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run BDAgent
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run egui
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run avast!
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run AVG8_TRAY
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run ISTray
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run K7SystemTray
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run K7TSStart
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run SpIDerMail
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run DrWebScheduler
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run OfficeScanNT
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run Monitor
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run SpamBlocker
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run Spam Blocker for Outlook Express
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run F-PROT Antivirus Tray application
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run RavTask
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run APVXDWIN
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run SCANINICIO
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run McENUI
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run MskAgentexe
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run Windows Defender
Step 10
Restart in normal mode and scan your computer with your Trend Micro product for files detected as WORM_PROLACO.EK If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Step 11
Scan your computer with your Trend Micro product to delete files detected as WORM_PROLACO.EK If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
Did this description help? Tell us how we did.

