ANDROIDOS_TROJDOWNLOADER.A
Malicious Downloader
Android OS


Threat Type: Trojan
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
This Android malware is able to evade Google’s Bouncer.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.

This Trojan poses as an app supposedly used to set wallpapers. However, it downloads another malicious file in the background. It then tricks users to install the downloaded file.
It was found in Google's Play Store. However, as of this writing Google has removed the said app from Play Store.
This Trojan may be manually installed by a user.
TECHNICAL DETAILS
Arrival Details
This Trojan may be manually installed by a user.
Download Routine
This Trojan connects to the following website(s) to download and execute a malicious file:
- http://dl.dropbox.com/u/{BLOCKED}8/Activator.apk
It connects to the following URL(s) to download its configuration file:
- http://dl.dropbox.com/u/{BLOCKED}9/srv.txt
NOTES:
This Trojan poses as an app supposedly used to set wallpapers. However, it downloads another malicious .APK file in the background and tricks users to install the downloaded file.
It starts a background thread to download a configuration file from Dropbox.
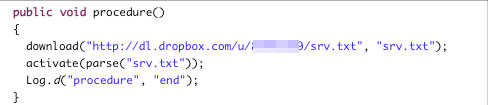
Contents of the downloaded configuration file point to URL where another malicious .APK file is downloaded:
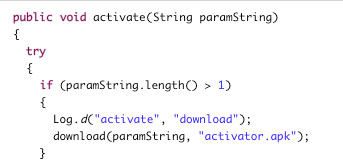
It then downloads the .APK file. Once the malicious .APK file is downloaded successfully, it launches the installer to install the downloaded file. It tricks the users into believing that the app is installing new wallpapers.
It was found in Google's Play Store. However, as of this writing Google has removed the said app from Play Store.
SOLUTION
Step 1
Trend Micro Mobile Security Solution
Trend Micro Mobile Security Personal Edition protects Android smartphones and tablets from malicious and Trojanized applications. The App Scanner is free and detects malicious and Trojanized apps as they are downloaded, while SmartSurfing blocks malicious websites using your device's Android browser.
Download and install the Trend Micro Mobile Security App via Google Play.
Step 2
Remove unwanted apps on your Android mobile device
Did this description help? Tell us how we did.

