ANDROIDOS_SNDAPPS.SM
Andr/Spy-E (Sophos); Android.Spyware.SndApps.A (Secure)
Information Stealer, Click Fraud
Android OS


Threat Type: Adware
Destructiveness: No
Encrypted: No
In the wild: Yes
OVERVIEW
This adware is found in application stores.
To get a one-glance comprehensive view of the behavior of this Adware, refer to the Threat Diagram shown below.
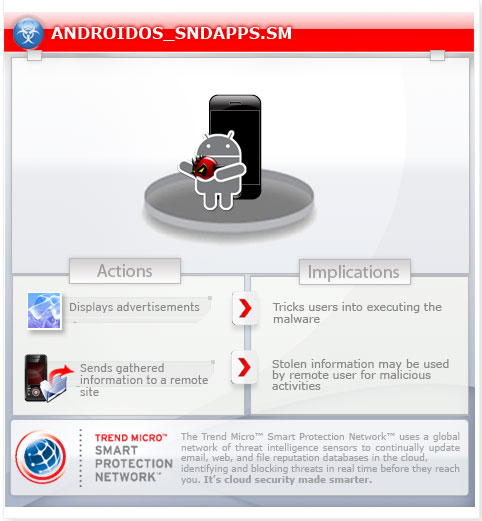
This adware displays unsolicited advertisements on an affected user's device. Upon execution, it gathers certain information. It then sends these information to a website.
It waits for a reply from the server which contains configuration about its adware routine. The reply may contain certain information.
Using the received configuration, this adware then proceeds with displaying a notification to the user which leads to the ad site.
If a user opens the notification, this adware also appends parameters, in encrypted format, to the ad site it visits. As such, the stolen information is disclosed to the ad site as well.
This adware may be manually installed by a user.
TECHNICAL DETAILS
Arrival Details
This adware may be manually installed by a user.
NOTES:
This is the Trend Micro detection for Trojanized Android applications containing malicious code that display unsolicited advertisements to infected victims' device.
Upon execution, it gathers the following information:
- Device ID (IMEI for GSM)
- User's mobile number
- Network Operator Name and Country Code
- Network Operator Country Code
- User's email address
It then sends these information to the following site:
- http://www.{BLOCKED}tudios.com/android_notifier/notifier.php?h={encrypted information}
It waits for a reply from the server which contains the configuration about its adware routine. The reply may contain the following information:
- Ad Delay time
- Ad site
- Lure money amount
- Notification ID
- Notification Text
- Notification Title
Using the received configuration, this adware then proceeds with displaying a notification to the user which leads to the ad site.
If a user opens the notification, this adware also appends the following parameters, in encrypted format, to the ad site it visits:
- &mobile_number={data}
- &email={data}
- &prize={data}
As such, the stolen information is disclosed to the ad site as well.
SOLUTION
Step 1
Before doing any scans, Windows XP, Windows Vista, and Windows 7 users must disable System Restore to allow full scanning of their computers.
Step 2
Scan your computer with your Trend Micro product to delete files detected as ANDROIDOS_SNDAPPS.SM. If the detected files have already been cleaned, deleted, or quarantined by your Trend Micro product, no further step is required. You may opt to simply delete the quarantined files. Please check this Knowledge Base page for more information.
NOTES:
The steps provided above are for cases when the malware is downloaded using a Windows PC.
TREND MICRO MOBILE SECURITY SOLUTION
Trend Micro has released an integrated solution for mobile devices, which provides automatic, real-time scanning to protect wireless devices against malicious code and viruses on the Web or hidden inside files. Download Trend Micro Mobile Security for Android.
Manual Removal Instructions
To manually remove the application on the infected device, uninstall the infected application by going to Settings > Applications > Manage Applications on your device.
Did this description help? Tell us how we did.


