What Happens When APTs Advance to Lateral Movement?
 Download the infographic: The Danger of Compromise
Download the infographic: The Danger of Compromise
Attackers are persistent and extremely resourceful. Should they begin to attack a target, it is only a matter of time before they find a flaw that will let them inside its network. Assuming the attack reaches the lateral movement stage of the campaign, what should companies always remember?
At this point, attackers have already established connections to their servers outside and are just trying to seek better vantage points they can use find more sensitive and profitable information. As attackers go deeper inside a network, the larger the impact they have to it. At this point, the attackers become like ninjas, virtually undetected by traditional security methods like free anti-malware and firewalls.
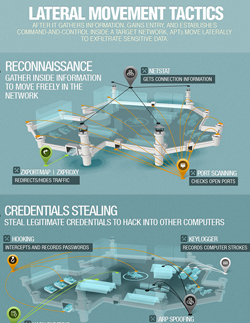
Lateral movement tactics used by attackers are mainly divided into three parts: the reconnaissance period where they gather inside information to move freely in a network, the stealing of legitimate credentials, and the actual intrusion to computers using these credentials.
Knowing what they're losing may be a company's final lifeline against targeted attacks in the lateral movement stage. Enterprises can still fight back by plugging the holes in their system.

Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- You Can't See Me: Achieving Stealthy Persistence in Azure Machine Learning
- Mitigating the Threat of Sidecar Container Injection
- Open RAN: Attack of the xApps
- Rise in Active RaaS Groups Parallel Growing Victim Counts: Ransomware in 2H 2023
- Apache APISIX In-the-wild Exploitations: An API Gateway Security Study
 MQTT and M2M: Do You Know Who Owns Your Machine’s Data?
MQTT and M2M: Do You Know Who Owns Your Machine’s Data? Building Resilience: 2024 Security Predictions for the Cloud
Building Resilience: 2024 Security Predictions for the Cloud Rise in Active RaaS Groups Parallel Growing Victim Counts: Ransomware in 2H 2023
Rise in Active RaaS Groups Parallel Growing Victim Counts: Ransomware in 2H 2023 Mitigating the Threat of Sidecar Container Injection
Mitigating the Threat of Sidecar Container Injection