Industrial Control System
Industrial control system (ICS) is a collective term used to describe different types of control systems and associated instrumentation, which include the devices, systems, networks, and controls used to operate and/or automate industrial processes. Depending on the industry, each ICS functions differently and are built to electronically manage tasks efficiently. Today the devices and protocols used in an ICS are used in nearly every industrial sector and critical infrastructure such as the manufacturing, transportation, energy, and water treatment industries.
There are several types of ICSs, the most common of which are Supervisory Control and Data Acquisition (SCADA) systems, and Distributed Control Systems (DCS). Local operations are often controlled by so-called Field Devices that receive supervisory commands from remote stations.
| Types of Industrial Control Systems | |
| Supervisory Control and Data Acquisition (SCADA) |
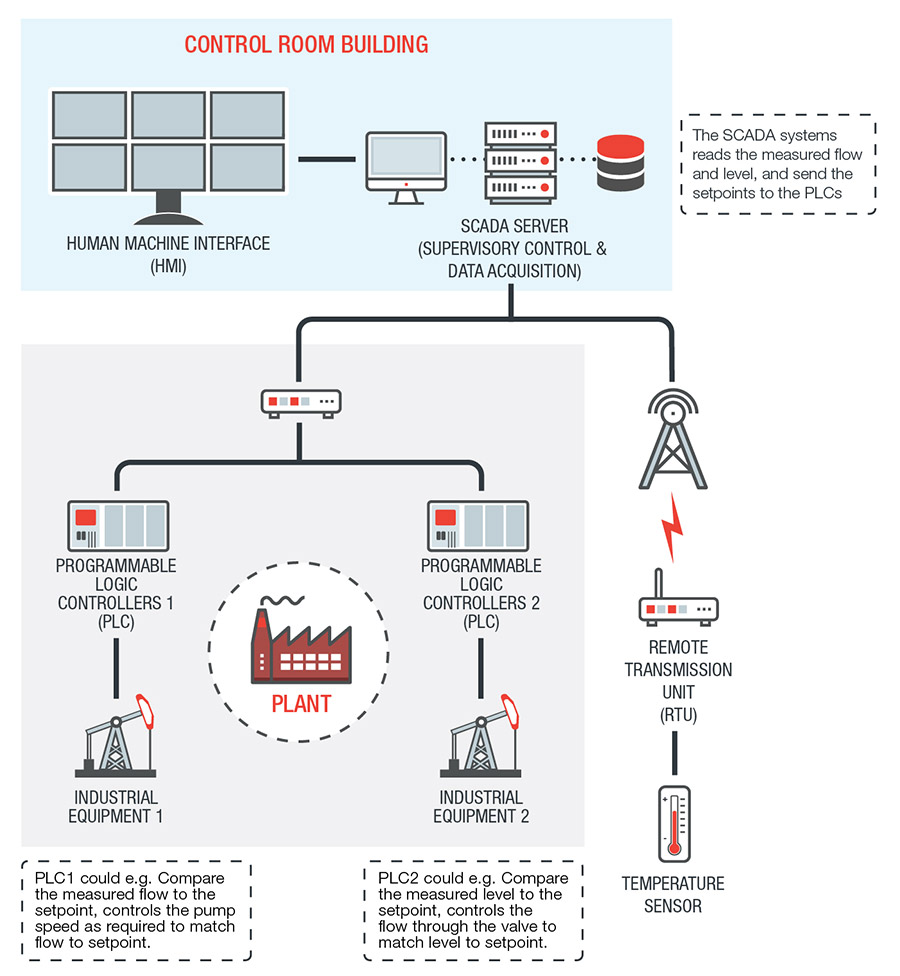
SCADA is not a system that can provide full control. Instead its capabilities are focused on providing control at the supervisory level. SCADA systems are composed of devices (generally Programmable Logic Controllers (PLC) or other commercial hardware modules) that are distributed in various locations. SCADA systems can acquire and transmit data, and are integrated with a Human Machine Interface (HMI) that provides centralized monitoring and control for numerous process inputs and outputs. The primary purpose of using SCADA is for long distance monitoring and control of field sites through a centralized control system. In lieu of workers having to travel long distances to perform tasks or gather data, a SCADA system is able to automate this task. Field devices control local operations such as opening or closing of valves and breakers, collecting data from the sensor systems, and monitoring the local environment for alarm conditions. SCADA systems are commonly used in industries involving pipeline monitoring and control, water treatment centers and distribution, and electrical power transmission and distribution. |
| Distributed Control System (DCS) |
This is a system that is used to control production systems that are found in one location. In a DCS, a setpoint is sent to the controller that is capable of instructing valves, or even an actuator, to operate in such a way that the desired setpoint is maintained. Data from the field can either be stored for future reference, used for simple process control, or even used for advanced control strategies with data from another part of the plant. Each DCS uses a centralized supervisory control loop to manage multiple local controllers or devices that are part of the overall production process. This gives industries the ability to quickly access production and operation data. And by using multiple devices within the production process, a DCS is able to reduce the impact of a single fault on the overall system. A DCS is also commonly used in industries such as manufacturing, electric power generation, chemical manufacturing, oil refineries, and water and wastewater treatment. |
| Actual ICS implementation |
Implementing an ICS environment may often be a hybrid of DCS and SCADA wherein attributes from both systems are incorporated. |
| Components of an Industrial Control System (ICS) Environment | |
| IT and OT |
Operational Technology (OT) variables include the hardware and software systems that monitors and controls physical devices in the field. OT tasks vary with every industry. Devices that monitor temperature in industrial environments are examples of OT devices The convergence of IT and OT provides enterprises greater integration and visibility of the supply chain– which include their critical assets, logistics, plans, and operation processes. Having a good view of the supply chain helps organizations remain competitive. On the flip side, however, the convergence of OT and IT allows easier access to these two components that are targets of cybercriminals. In many organizations OT infrastructure is at best poorly protected against cyber attacks. |
| Programmable Logic Controller (PLC) |
This is a type of hardware that is used in both DCS and SCADA systems as a control component of an overall system. It also provides local management of processes being run through feedback control devices such as sensors and actuators. In SCADA, a PLC provides the same functionality as Remote Terminal Units (RTU). In DCS, PLCs are used as local controllers within a supervisory control scheme. PLCs are also implemented as primary components in smaller control system configurations. |
| Remote Terminal Unit (RTU) |
An RTU is a microprocessor-controlled field device that receives commands and sends information back to the MTU. |
| Control Loop |
Every control loop consists of hardware such as PLCs and actuators. The control loop interprets signals from sensors, control valves, breakers, switches, motors, and other similar devices. The variables measured by these sensors are then transmitted to the controller to carry out a task and/or complete a process. |
| Human Machine Interface (HMI) |
A graphical user interface (GUI) application that allows interaction between the human operator and the controller hardware. It can also display status information and historical data gathered by the devices in the ICS environment. It is also used to monitor and configure setpoints, control algorithms, and adjust and establish parameters in the controllers. |
| Remote Diagnostics and Maintenance |
This is a term used to identify, prevent, and recover from abnormal operations or failures. |
| Control Server |
A control server hosts the DCS or PLC supervisory control software and communicates with lower-level control devices. |
| SCADA Server or Master Terminal Unit (MTU) |
This is a device that issues commands to RTUs in the field. |
| Intelligent Electronic Device (IED) |
A smart device capable of acquiring data, communicating with other devices, and performing local processing and control. The use of IEDs in control systems like SCADA and DCS allows for controls at the local level to be done automatically. |
| Data Historian |
A data historian is a centralized database for logging all process information within an ICS environment and then exporting data to the corporate IS. The data gathered is then used for process analysis, statistical process control, and enterprise level planning. |
What is an ICS System?
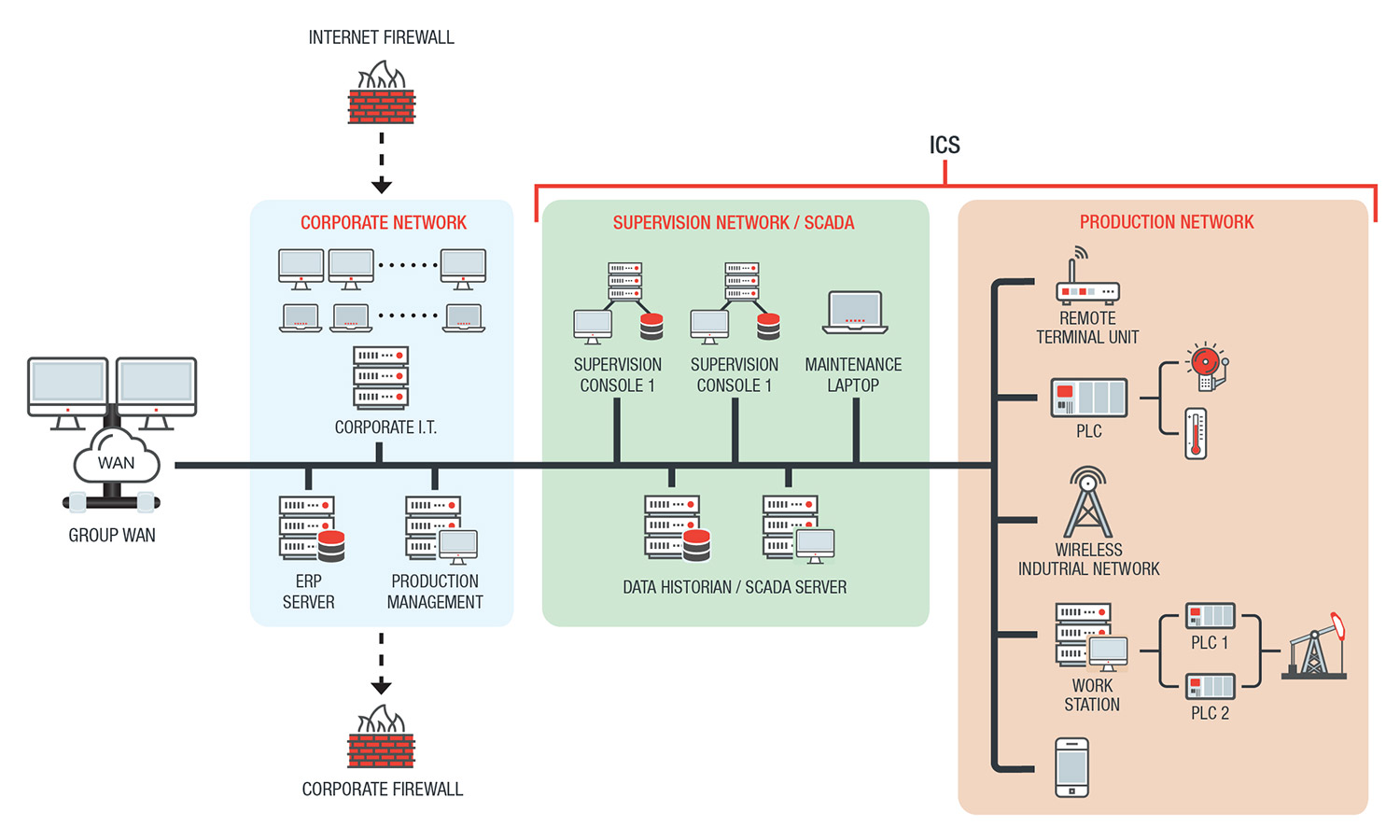
What function does a SCADA system fulfill
Communication within ICS Systems
Devices and control modules in ICS systems relay information through communication protocols. There are several communication protocols used through various ICS environments. Most of these protocols are designed for specific purposes such as process automation, building automation, power systems automation, and many more. These protocols were also developed to ensure interoperability between different manufacturers. However, there are some protocols that only work if the protocols and equipment come from the same manufacturer. The ICS protocols that are commonly found include:
| Process Field Bus (PROFIBUS) |
PROFIBUS uses RTU to MTU, MTU to MTU, and RTU to RTU communications in the field. There are two available variants: Profibus DP (decentralized peripherals), which is used to operate sensors and actuators through a central controller, and Profibus PA (process automation), which is used to monitor measuring equipment through a process control system. |
| Distributed Network Protocol (DNP3) |
This is a protocol with three layers operating at the data link, application, and transport layers. This protocol is widely used in electricity and/or water and wastewater treatment plants. |
| Modbus |
Since its introduction in 1979, the Modbus is considered one of the oldest ICS protocols. Modbus uses serial communications with the PLCs and has been the de facto communications protocol in an ICS environment. There are two types of Modbus implementations: Serial Modbus – which uses the high-level data link control (HDLC) standard for data transmission, and Modbus-TCP – which uses the TCP/IP protocol stack to transmit data. |
| Open Platform Communication (OPC) |
The OPC is a series of standards and specifications for industrial communications. The OPC specification is based on technologies developed by Microsoft® for the Windows® operating system family (OLE, COM, and DCOM). |
| Building Automation and Control Networks (BACnet) |
This is a communication protocol that is designed to control heating, ventilating, and air-conditioning control (HVAC); lighting; building access; and fire detection. |
| Common Industrial Protocol (CIP) |
A CIP is a set of services and messages for control, security, synchronization, configuration, information, and so forth. The ICP can be integrated into Ethernet networks and the internet. CIP has a number of adaptations providing intercommunication and integration for different types of networks. |
| Ethernet for Control Automation Technology (EtherCAT) |
An open-source communications protocol used to incorporate Ethernet into industrial environments. EtherCAT is used in automation applications with short updating cycles (≤ 100μs) and with jitter ≤ 1μs. |
Common Threats to Industrial Control Systems
In order to improve system functions and productivity, every ICS constantly incorporates new technologies and software in both IT and OT. With IT and OT merged, they become bigger targets for cybercriminals. One of the common flaws of security solutions used in OT infrastructure is its inability to protect legacy control systems such as SCADA. In addition to that, organizations also have to face the rise of security challenges in new and emerging technologies, such as cloud computing, big data analytics, and the internet of things (IoT). Centralization introduces new and unknown vulnerabilities into the cyber ecosystem.
[Related: Why do attackers target industrial control systems?]
Attacks on ICS systems are often targeted attacks that use the ICS entry path to gain a foothold inside a system which will allow them to laterally move into the organization. Among the most high-profile cases are the Stuxnet worm, which was used to manipulate centrifuges inside nuclear facilities in Iran, and BlackEnergy, which affected power generation facilities in Ukraine. Despite most of the attacks focusing on data theft and/or industrial espionage, both of the aforementioned cases demonstrated how malware had a kinetic effect. The Trend Micro whitepaper titled Cyber Threats to the Mining Industry explores how the mining industry is increasingly becoming a target of cyber espionage campaigns. These cyber espionage campaigns are designed to gain the latest technical knowledge and intelligence that will help some interest groups thrive and maintain competitive advantage.
[Read: Protecting ICS: Defensive strategies for industrial control systems]