Sextortion Scheme Deployed by ChaosCC Hacker Group Demands US$700 in Bitcoin
 A recently discovered email scheme reportedly deployed by a hacking group called ChaosCC claims to have hijacked recipients’ computers and recorded videos of them while watching adult content. As reported by Bleeping Computer, this sextortion scheme attempts to trick recipients into paying US$700 in bitcoin.
A recently discovered email scheme reportedly deployed by a hacking group called ChaosCC claims to have hijacked recipients’ computers and recorded videos of them while watching adult content. As reported by Bleeping Computer, this sextortion scheme attempts to trick recipients into paying US$700 in bitcoin.
How the scheme plays out
The sextortion scheme involves an email sent to a potential victim by someone claiming to be from the ChaosCC hacker group (not to be confused with the Chaos Computer Club white-hat hacker group).
As with previous scams with a similar modus operandi, the email starts by informing the recipient that their account has been compromised by the email sender. The email tries to further scare the recipient by referring to their “intimate adventures” on the internet.
The email continues to instill fear on the recipient by saying that as they browse adult websites, their device’s camera turns on automatically and takes a video of them and the content they’re watching. The email claims that the recorded video clip is automatically saved on the hacker group’s server. It then warns that if the recipient fails to send US$700 to the sender’s bitcoin wallet, the video will be sent to the recipient’s contacts.
The email ends with a piece of mocking advice: The recipient is told to cover their device’s camera with a sticker when visiting adult websites.
[Read: Digital Extortion: A Forward-Looking View]
Sextortion schemes on the rise
In line with Trend Micro’s predictions for the year and as noted in Trend Micro’s 2019 midyear security roundup, there has been a surge in cases of sextortion deployed via email. Trend Micro’s detections of sextortion-related spam emails increased by 318% from the second half of 2018 (2,188,415) to the first half of 2019 (9,160,856).
Just last April, two of Trend Micro’s researchers, Loseway Lu and Marshall Chen, discovered a sextortion scheme that demanded bitcoin payments from targeted Italian-speaking users. Based on the IP lookups of the spam emails’ senders, the emails in this scheme appear to have been sent using the Gamut spam botnet.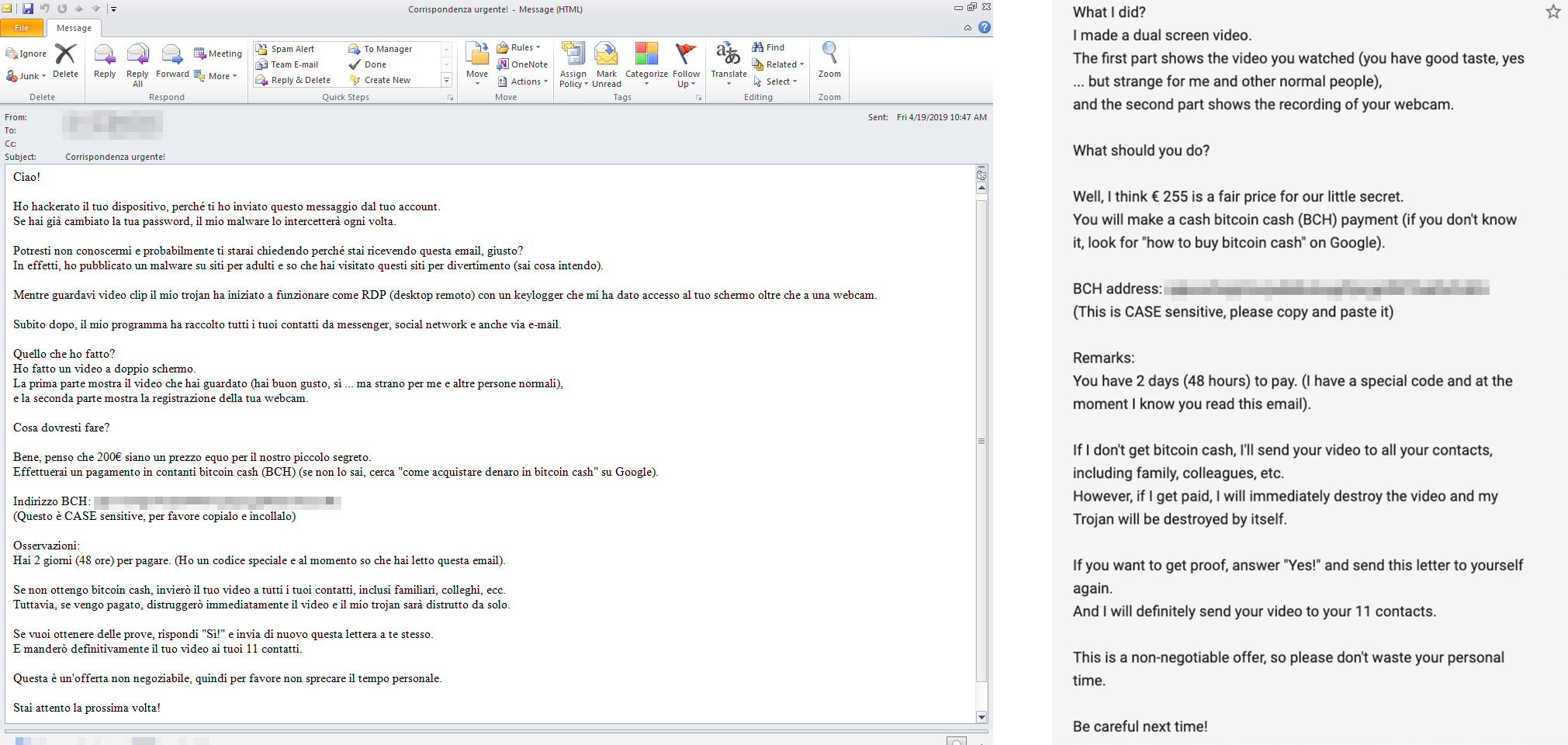
Figure 1. A sample sextortion email that targets Italian-speaking users (left) and its partial English translation (right)
[Read: 2.4 Million Credential Phishing Attacks Detected and Blocked in 2019 1H]
Security recommendations
Operators of sextortion schemes use fear to intimidate victims into giving in to their demands. To avoid falling for sextortion schemes, users should adopt the following best practices:
- Don’t pay and respond. If you receive a sextortion email, you should immediately report it to authorities.
- Make sure that your personal data is shared on or stored in secure platforms.
- Reduce the risk of getting your accounts compromised by regularly updating your credentials and accounts.
- Closely examine URLs and attachments in emails before clicking or downloading them.
Organizations, for their part, can consider adopting the Trend Micro™ Cloud App Security™ solution, which can help detect and block even the most convincing phishing attempts. It uses machine learning to perform sender, content, and URL reputation analysis. In addition, it detects suspicious content in the message body and attachments, and provides sandbox malware analysis and document exploit detection.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks Today’s Cloud and Container Misconfigurations Are Tomorrow’s Critical Vulnerabilities
Today’s Cloud and Container Misconfigurations Are Tomorrow’s Critical Vulnerabilities Ransomware Spotlight: INC
Ransomware Spotlight: INC The Realities of Quantum Machine Learning
The Realities of Quantum Machine Learning