What Happens During a Ransomware Attack?
Ransomware damages critical data
Ransomware is devastating for a business because it damages critical data. During an attack, ransomware scans for important files and encrypts them with strong encryption that cannot be reversed, crippling an organization faster than other malicious applications.
How a ransomware threat begins
Most ransomware attacks start with a malicious email. The email often contains a link to an attacker-controlled website where the user downloads the malware. It could also contain a malicious attachment with code that downloads ransomware after the user opens the file.
Attackers usually use Microsoft Office documents as attachments. Office has a Visual Basic for Applications (VBA) interface that attackers use to program scripts. Newer Office versions disable the feature that automatically runs macro scripts when a file opens. The malware prompts the user to run the scripts, and many users do. This is why malicious macros are still dangerous.
The Office macro downloads the ransomware from an attacker’s server, and the malware runs on the local device. The ransomware scans the network and local storage for critical files and encrypts what it finds. Encryption is typically symmetric Advanced Encryption Standard (AES) cryptography using 128 or 256 bits. It makes the process resistant to brute-force attacks. Some ransomware also uses public / private key cryptography such as Rivest-Shamir-Adleman (RSA).
Recovering data and removing ransomware
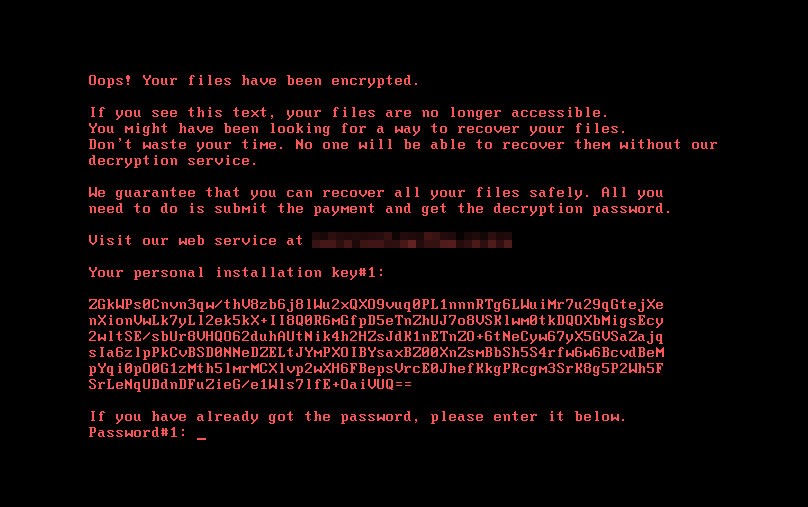
Ransomware developers build in functionality that blocks users from removing the application without first paying the ransom. Some hackers use screen lockers so users cannot access the Windows desktop. Because the cryptography libraries used to encrypt files are secure, removing the malware still leaves data encrypted and inaccessible.
The FBI advises affected businesses not to pay the ransom. Other experts say that paying the ransom has resulted in file decryption. Sometimes the attackers do not deliver the decryption key even after the ransom is paid. The targeted business is then left with no files and a monetary loss. You can remove the ransomware, but it is unlikely you’ll be able to recover the files without paying the ransom unless you have a backup.
Most anti-malware vendors have patches or downloadable solutions that remove ransomware. After clearing the malware, you can restore files from a backup. You can also restore the computer to factory settings. With the latter solution, your computer returns to the same state as when you first bought it. You would need to reinstall any third-party software.
Sophos Group, a British security company, identified Ryuk’s attack flow, which is also called the attack kill chain. See the diagram below.
Ransomware protection
You can protect devices and data from ransomware in several ways. Since infection usually starts with a malicious email message, start with anti-malware cybersecurity that scans incoming messages for suspicious links or attachments. If found, quarantine the messages, keeping them from reaching user inboxes.
Content filtering on the network is also effective. It stops users from accessing attacker-controlled websites. Combined with email filters, content filtering is an effective way to stop ransomware and most malware from accessing your internal network.
Anti-malware software should run on all network devices including smartphones. Anti-malware stops ransomware from encrypting files and removes it from the system before it sends the payload. If the organization has a bring-your-own-device (BYOD) policy, it is important to run an approved anti-malware application on user devices.
User training is a proactive way to protect from ransomware. Since ransomware often starts with phishing and social engineering, users trained to identify attacks are a good addition to other anti-malware measures. Combined, training and anti-malware systems greatly reduce cybersecurity risk. If anti-malware systems fail, users trained to identify an attack are not tricked into running malicious executables.
Ransomware examples
Several types of ransomware still affect businesses, even though the malware’s global threat was generally removed. They exist to extort money from individuals or businesses that don’t have effective protection in place.
One of the first known ransomware applications that made a global impact was CryptoLocker. CryptoLocker targeted Windows machines and was widespread in 2014. Infection usually started with an email and a malicious attachment. The software then encrypted important files with asymmetric (RSA) public / private key encryption.
Locky is an example of ransomware that used social engineering. Released in 2016, Locky started with a malicious Word document attached to an email. When users opened the file, the content looked scrambled except a message to turn on macros. After users turned on macros and opened the file again, Locky executed.
Bad Rabbit is an example of malware that users voluntarily downloaded. It was normally spread by pretending to be an Adobe Flash update. After the malware ran, it encrypted the files and the system rebooted. Bad Rabbit restricted booting the computer and instead displayed a message that a ransom must be paid to decrypt the files.
Preventing ransomware
The above examples are just a few ransomware versions that still plague organizations. Ransomware developers continue to create new ways to hold files hostage for a ransom. If you understand how ransomware works, you can implement the right defenses. You can prevent ransomware with an effective anti-malware solution, user training, and email filters that block malicious messages.
Related Research
Related Articles