CHALLENGES
Securing a dispersed cloud environment
Complex hybrid cloud environments
Business transformation doesn’t happen overnight – it takes time. During the transition, you’ll have a mix of technologies that can be complex for teams to secure as risks are uncovered.
Too many tools create silos
Point products create visibility silos across your hybrid cloud environment. Security gaps can result from these silos, and teams lose valuable time investigating critical alerts and incidents.
Continuous cloud compliance
Compliance audits and cloud governance are daunting tasks. Not only are there more servers, data, workloads, and applications, but they’re also constantly in flux. Ensuring compliance with frameworks such as NIST and PCI requires security tools built to manage the unique characteristics of hybrid cloud environments.
Discover what other challenges cybersecurity professionals encountered
Secure your continuously evolving cloud environment
Trend Vision One™ – Cloud Security protects your data no matter your environment, from cloud-native to hybrid, on-prem, multi-cloud, and containers
Hybrid focus
Apply modern security tooling to any hybrid workload, whether on-prem or in the cloud.
Multi-cloud complexity
Provide consistent security policy, risk assessment, and security controls regardless of where workloads are running—AWS, Microsoft Azure, Google Cloud Platform (GCP), multi-cloud, or on-premises.
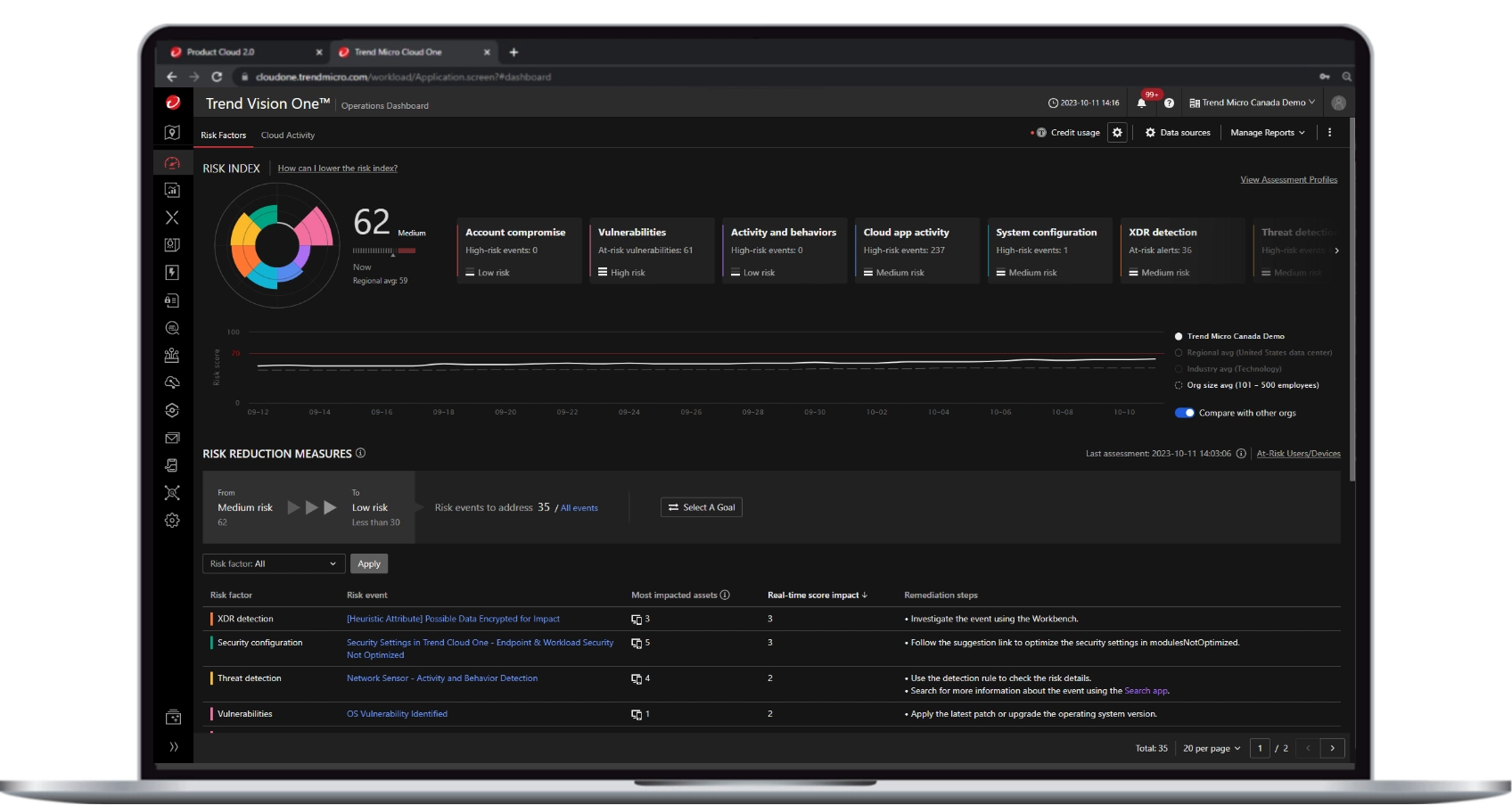
Measuring risk
Identify blind spots, manage the cloud attack surface, and improve security posture.
Incident handling
Ensure SOC visibility, easy prioritization, and contextual awareness of cloud attacks.
All your Cloud Security in one place
Cloud Protection
On-demand and runtime protection for hybrid cloud. Discover and block vulnerabilities and malware across all workloads: servers, containers, pipelines, IAC storage, virtual private cloud, and databases
Attack Surface Risk Management
Take charge of your cyber risk with cloud-focused internal and external attack surface discovery, real-time assessments, risk prioritization, and remediation.
XDR for Cloud
Trend Vision One – XDR for Cloud extends detection and response to customer cloud accounts by examining user, service, and resource log activity for suspicious behavior and providing remediation and response actions.
Explore related sources
JOIN 500K+ GLOBAL CUSTOMERS
Get started with the World’s #1 Cloud Security Platform









