What Is XDR? (Extended Detection and Response)
XDR
Stealthy threats evade detection. They hide between security silos and disconnected solution alerts, propagating as time passes. In the meantime, overwhelmed security analysts try to triage and investigate with narrow, disconnected attack viewpoints.
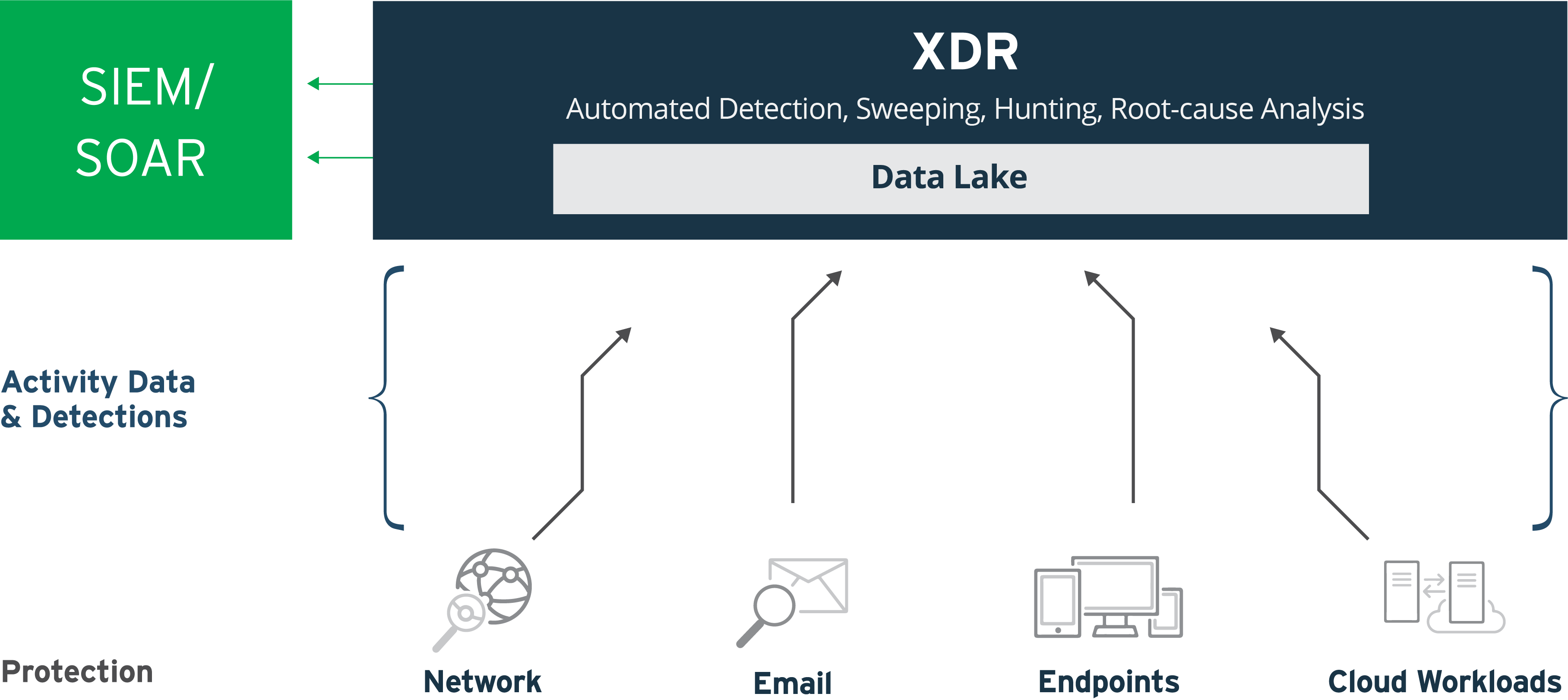
XDR breaks down these silos using a holistic approach to detection and response. XDR collects and correlates detections and deep activity data across multiple security layers – email, endpoint, server, cloud workloads, and network. Automated analysis of this superset of rich data detects threats faster. As a result, security analysts are equipped to do more and take quicker action through investigations.
Learn more about the security layers that can feed into XDR.
XDR security
XDR (Extended Detection and Response) security is a holistic approach that integrates data from various sources like endpoints, networks, and cloud environments into a unified platform. This comprehensive integration enhances threat detection by correlating data across different layers, utilizing advanced analytics and machine learning. XDR Security allows for faster detection of threats and improved investigation and response times through security analysis.
SOC challenges
When it comes to detection and response, security operations center (SOC) analysts are faced with a daunting responsibility. They must quickly identify critical threats to limit risk and damage to the organization.
Investigation Challenges
Investigations are often manual and time-consuming due to abundant logs and unclear indicators. XDR automates threat investigations, providing rich data and tools for analysis, such as automated root cause analysis, which shows attack timelines and paths across various security layers.
Alert overload
It is no surprise that IT and security teams are often overwhelmed with alerts coming from different solutions. A company with an average of 1,000 employees can see a peak of up to 22,000 events per second enter their security information and event management (SIEM) system. That’s almost 2 million events in a day.[1] They have limited means in which to correlate and prioritize these alerts, and struggle to quickly and effectively weed through the noise for critical events. XDR automatically ties together a series of lower-confidence activities into a higher-confidence event, surfacing fewer and more prioritized alerts for action.
Visibility gaps between security solutions
Many security products provide visibility into activity. Each solution offers a specific perspective and collects and provides data as relevant and useful for that function. Integration between security solutions can enable data exchange and consolidation. The value is often limited by the type and depth of the data collected and the level of correlated analysis possible. This means there are gaps in what an analyst can see and do. XDR, by contrast, collects and provides access to a full data lake of activity across individual security tools, including detections, telemetry, metadata, and netflow. Applying sophisticated analytics and threat intelligence, XDR provides the full context needed for an attack-centric view of an entire chain of events across security layers.
Difficulty undertaking investigations
Faced with many logs and alerts but no clear indicators, it’s difficult to know what to look for. If you find an issue or threat, it’s hard to map out its path and impact across the organization. Performing an investigation can be a time-consuming, manual effort, if there are even the resources to do it. XDR automates threat investigations by eliminating manual steps and provides rich data and tools for analysis that would otherwise be impossible. Consider, for example, automated root cause analysis. An analyst can clearly see the timeline and attack path that may cross email, endpoints, servers, cloud workloads, and networks. The analyst now can assess each step of the attack to enact the necessary response.
Slow detection and response times
The result of these challenges is that threats go undetected for too long, increasing response time and raising the risk and consequences of an attack. XDR ultimately leads to much-needed improvements in threat detection rates and response times. Increasingly, security organizations are measuring and monitoring mean-time-to-detect (MTTD) and mean-time-to-respond (MTTR) as key performance metrics. Likewise, they evaluate solution value and investments in terms of how they drive these metrics and thus reduce the enterprise’s business risks.
XDR vs. EDR
XDR represents the evolution of detection and response beyond the current point-solution, single-vector approach.
Clearly, endpoint detection and response (EDR) has been enormously valuable. However, despite the depth of its capability, EDR is restricted because it can only detect and respond to threats inside managed endpoints. This limits the scope of threats that can be detected as well as the view of who and what is affected. These restrictions ultimately limit response effectiveness within the SOC.
Likewise, network traffic analysis (NTA) tools’ purview is limited to the network and monitored network segments. NTA solutions tend to drive a massive number of logs. The correlation between network alerts and other activity data is critical to make sense and drive value from network alerts.
Augmenting the SIEM
Organizations use SIEMs to collect logs and alerts from multiple solutions. While SIEMs allow companies to bring together a lot of information from multiple places for centralized visibility, they result in an overwhelming number of individual alerts. Those alerts are difficult to sort through and understand what is critical and needs attention. Correlating and connecting all of the information logs to gain a view of the larger context is challenging with just a SIEM solution.
Conversely, XDR collects deep activity data and feeds that information into a data lake for extended sweeping, hunting, and investigation across security layers. Applying AI and expert analytics to the rich data set enables fewer, context-rich alerts, which can be sent to a company’s SIEM solution. XDR doesn’t replace the SIEM, it augments it – reducing the time required by security analysts to assess relevant alerts and logs and decide what needs attention and warrants deeper investigations.
Capability imperatives
Multiple security layers beyond the endpoint
- To perform extended detection and response activities, you need at least two layers, and the more the better; endpoint, email, network, servers, and cloud workload.
- XDR feeds activity data from multiple layers to a data lake. All applicable information is made available for effective correlation and analysis in the most relevant structure.
- Pulling from a single vendor’s native security stack prevents vendor/solution proliferation. It also provides for an unmatched depth of integration and interaction between detection, investigation, and response capabilities.
Purpose-built AI and expert security analytics
- Collecting data is one benefit of XDR, but applying analytics and intelligence to drive better, faster detection is critical.
- As collecting telemetry becomes a commodity, security analytics, combined with threat intelligence, drive value that can turn information into insight and action.
- An analytics engine fed by native, intelligent sensors offers more effective security analytics than can otherwise be achieved on top of third-party products and telemetry. Any given vendor will have a much deeper understanding of their own solutions’ data than a third-party’s data. You can ensure optimized analytical capabilities by giving priority to XDR solutions that are purpose-built for a vendor’s native security stack.
Single, integrated and automated platform for complete visibility
- XDR enables more insightful investigations because you can make logical connections from the data provided within a single view.
- Having a graphical, attack-centric timeline view can provide answers in one place, including:
- How the user got infected
- What was the first point of entry
- What or who else is part of the same attack
- Where the threat originated
- How the threat spread
- How many other users have access to the same threat
- XDR augments security analysts’ capabilities and streamlines workflows. It optimizes teams’ efforts by speeding up or removing manual steps, and enables views and analyses that can’t be done in media
- Integration with SIEM and security orchestration, automation and response (SOAR) enables analysts to orchestrate XDR insight with the broader security ecosystem.
Trend Micro's XDR Solution
Native XDR is in. Open XDR is out.
Using XDR, hunt, detect, investigate, and respond to threats from a single security platform.
Related Articles