Malware
Trend Micro Collaborated with Interpol in Cracking Down Grandoreiro Banking Trojan
In this blog entry, we discuss Trend Micro's contributions to an Interpol-coordinated operation to help Brazilian and Spanish law enforcement agencies analyse malware samples of the Grandoreiro banking trojan.
Last April 2023, the International Criminal Police Organisation (Interpol) requested any indicators of compromise (IOCs) or information related to the banking trojan Grandoreiro, specifically for command-and-control (C&C) servers. Grandoreiro has evolved with new features and capabilities since it first appeared around 2018, and has been primarily targeting users in Latin America and Europe. Trend Micro was one of the partners involved in Interpol’s operation to help Brazilian and Spanish law enforcement agencies (LEAs) analyse Grandoreiro malware samples as part of their national cybercrime investigations. The Interpol-coordinated operation resulted in the arrest of five administrators behind a Grandoreiro operation, as announced by the Brazilian authorities.
Grandoreiro spreads through phishing emails, malicious attachments, or links leading to fake websites. These emails often impersonate legitimate organisations, such as banks or financial institutions, to trick users into downloading and executing the malware. Once installed on a victim’s system, Grandoreiro operates as a typical banking trojan, aiming to steal sensitive financial information. Over time, Grandoreiro has undergone various updates and modifications, enhancing its evasion techniques and obfuscation methods to evade detection by antivirus software and security measures.
Trend’s Contributions
Here’s the summary of Trend’s contributions to the operation:
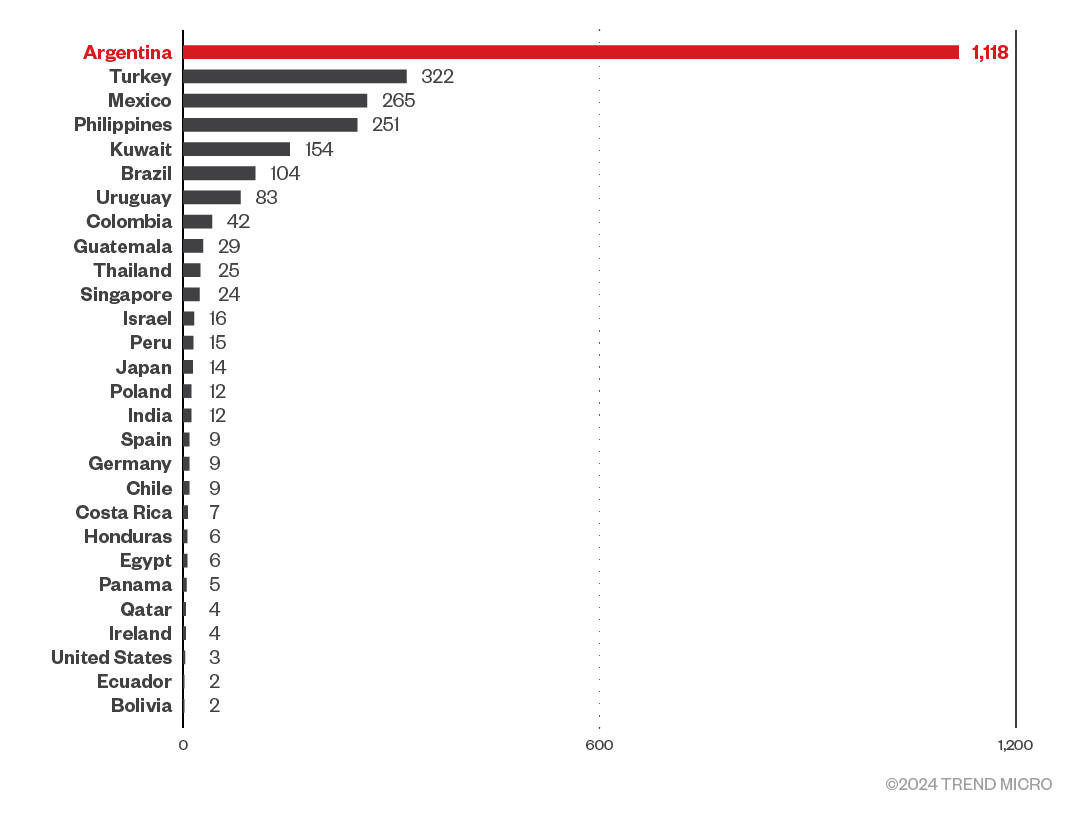
- Trend threat intelligence data from January to April 2023 showed that Argentina recorded the highest number of detections related to Grandoreiro with 1,118 detections, followed by Turkey with 322 detections, and Mexico with 265 detections (Figure 1).
- Trend provided an additional list of banks/strings found on a sample. These were utilised to monitor the browsing activity of the user by cross-referencing the window to check if it matches specific strings. The list of strings can be accessed at the end of this article.
- During the investigation, it was discovered that Grandoreiro utilised domain generation algorithms (DGAs) for its C&C communications. To gain further insights, Trend generated all possible domains from the list of strings and subdomains found on multiple samples. As a result, more than 4,000 DGAs were generated, providing valuable information to pivot to the C&C servers used by Grandoreiro at that time.
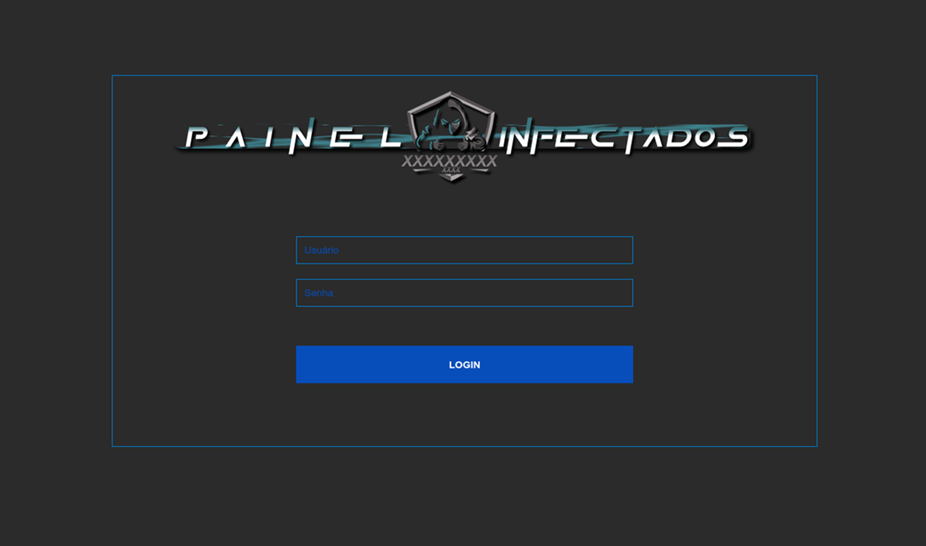
- The admin panel is crucial for investigation on the scale of attack of threat actors and the identification of victims. Using the open-source tool URLScan (urlscan.io), Trend recommended inspecting three active admin panels with their respective locations. The following were the URLs of the admin panels and the screenshot of login page (Figure 2):
- 185.191.228[.]227/autorizar.php (United States)
- 192.95.6[.]196/23112022new/autorizar.php (Canada)
- 51.77.193[.]20/eliteseguros/autorizar.php (France)
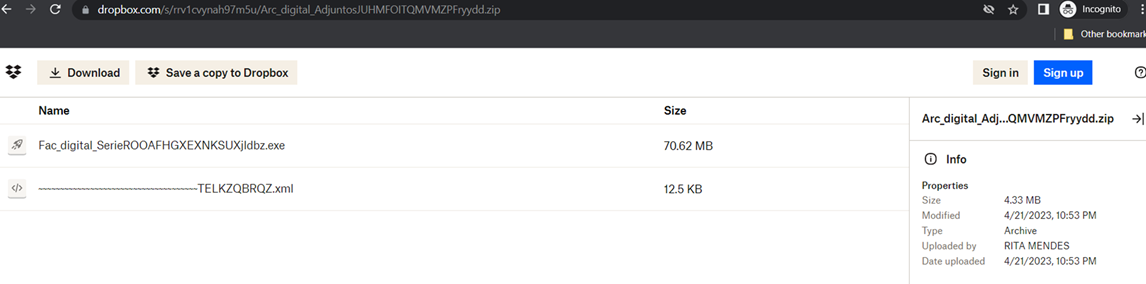
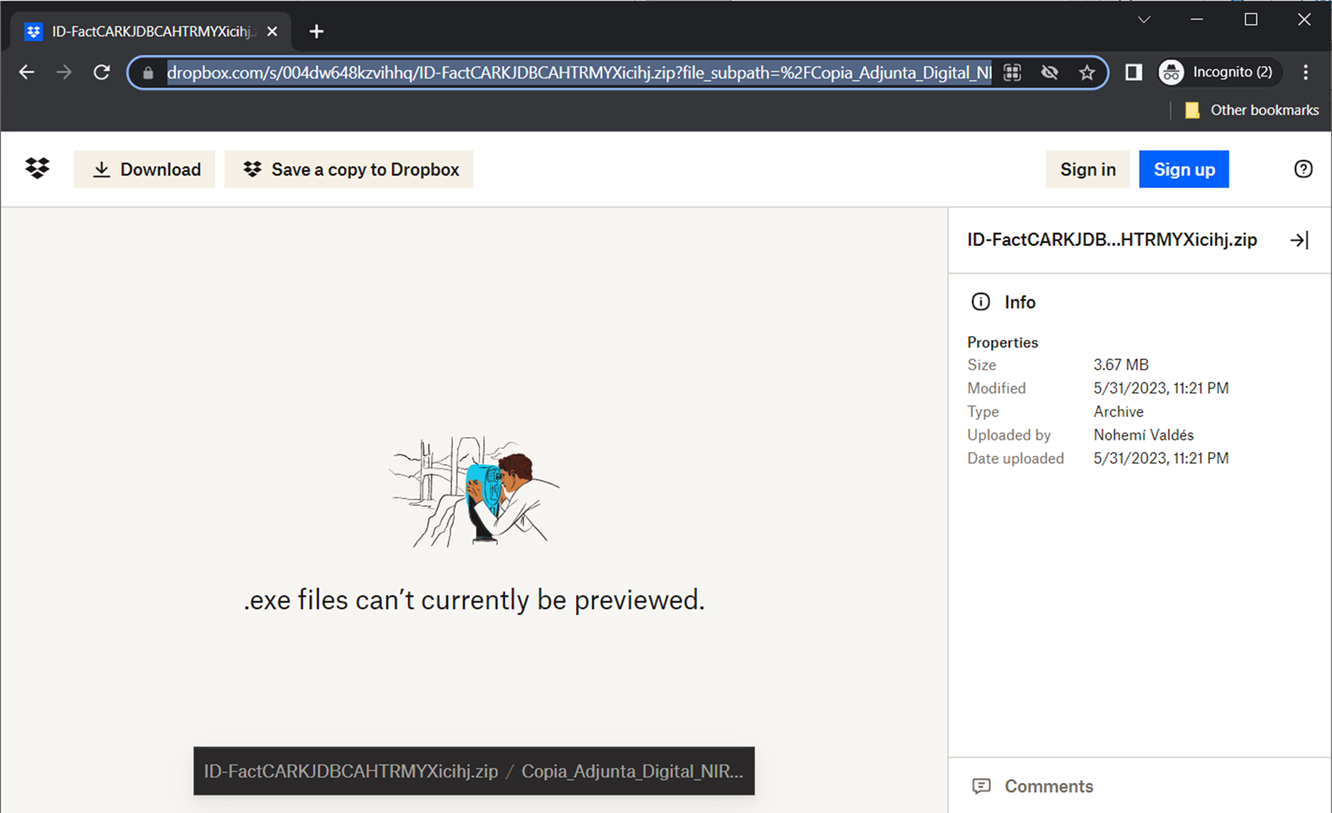
- Trend recommended to inspect the file storage Dropbox where the malicious email attachment was hosted and contained a name of the uploader. It was highly likely a fake name although we believe it can help in attribution. Figures 3 and 4 show the Dropbox accounts with the names “RITA MENDES” and “Nohemi Valdes”, respectively:
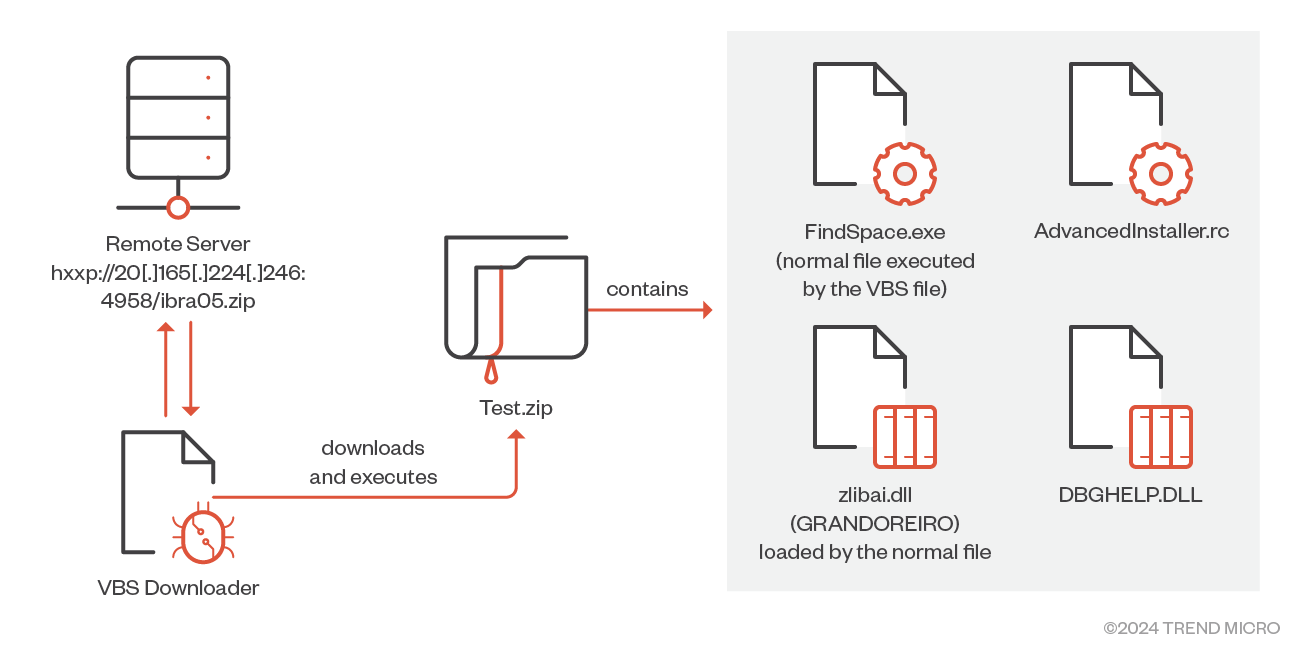
- Trend provided an analysis of Grandoreiro’s utilisation of VBScript (VBS) for its malicious routine, as shown in Figure 5.
Cooperation with Interpol
These contributions are the latest in Trend’s long track record of successful collaborations with international law enforcement. Collaborations between law enforcement and the private sector provide security organisations and industry specialists the opportunity to share their expertise, resources, and years-long experience with LEAs such as Interpol to enhance their cybercrime combating efforts in effectively targeting and dismantling malicious actors.
Trend’s ongoing cooperation with Interpol has been instrumental in a series of prominent crackdowns throughout the years: These include the dismantling of the 16shop phishing kit and the disruption of African cybercrime networks during Africa Cyber Surge I and II in 2023, the apprehension of business email compromise (BEC) actors under Operation Killer Bee in 2022, and the capture of REvil and Cl0p syndicate members as part of Operation Cyclone in 2021. This partnership endures as Trend persists in its commitment to securing our increasingly connected world.
The list of banks/strings found on a sample can be viewed here.

